The origin of the Internet also saw the dawn of a new tool, immediate publication; before the Internet in order to convey ideas in a written medium, it was required to publish your works on paper, and these works would need to go through an editing process, and would be tailored for an audience over time, and multiple drafts, before being shown to the world. With the Internet, you can press a button that says “post”, “comment” “send”, or “tweet”, and whatever was typed in the last few seconds is sent out into the world, visible to a large group of people. What happened because of this was a huge blast of publicity, and a rising sea of questions about privacy.
When it comes to privacy on the Internet three camps have arisen. The Facebook generation, and a variety of other tech-savvy individuals, who claim that Internet privacy is as easy as clicking for higher privacy settings on Facebook, using incomplete versions of your full name, and simply adapting the technology available. Another, the journalists, politicians and more tentative, saying that those measures are not enough, government intervention is needed as data is out of user control and in the hands of the corporations. And the final, who rave that people are not the issue, it is corporations, governments and organizations that can and are misusing the information of this age to hurt us. Now I don’t think any one of these groups is right, or wrong, but instead I feel like most of Internet privacy isn’t the program, the Internet or the government’s fault, nor is it because of the users around you, it is you yourself who carries the blame.
I have a story to share. It starts with a simple Google search, typing my own name into the world wide web, and within a tenth of a second after pushing the enter key I can see (in descending order):
- My home town, and the street I live on, with the names of my family right next to mine (although they are merely related people, it’s not too far of a stretch)
- A verification that there is only 1 of me in the US, with the origins of my name
- My Google + account, with a list of everywhere I have ever traveled, with my gender, list of friends, and who is in my circles. (all seen without logging on to Gmail or other such identification) I did quickly change my Google settings immediately after this.
- Another list of family members
- A web site post I made from freshman year of high school, only my name appears, and some thoughts on single sex educational facilities
- A history of people who looked at the site above, gives an alias that I used in high school as a user name for myself
- My Google plus friends page, with my page linked to it
- A post on another blog about my team winning a history competition
Thanks to: (www.google.com, www.whitepages.com)
And that’s only in the first 8, on the next page, for $10 I could see my whole history from my great grandfather on my mother’s side coming to America, and the Great, great grandmother on my father’s side coming to America.
This is a ton of data about me, even though I am not on Facebook, not on twitter, or engaged in almost anything.
Now the results of this search aren’t particularly scary, it isn’t startling and it isn’t horrifying to you the audience. I as a person am not endangered, and can safely browse the web at night without worries that someone armed with my data will attack me with it.
However, this situation is easily reversed; when looking at my Google + page, the only reason that I didn’t learn more about myself is that I don’t ever use Google +, Facebook or any other such sites. Had I used these I may have had dozens of results that would have shown more about exactly who or where I was. The key to Internet privacy isn’t are you on the Internet, its how much you publish, and what you publish.
To illustrate: As of March of this year,
“Twitter now has “more than 140 million active users” sending a heady 340 million tweets each and every day. Or, in another words, over a billion tweets every 72 hours.” –Shea Bennet
And that’s just twitter from a few months ago, it has only become more popular. (Check out these stats to learn more about the amount of data and messages sent everyday by everyone, although we are going to focus on twitter for this example). But more about these tweets; Given that twitter has 500 million registered users, but only 175 million active users (thanks to this helpful site) and assuming the same number of tweets are made as when it only had 140 million users (a very conservative estimate), and the number of posts by active users is equally spread, this means that people are making at a minimum two tweets an hour (like I said a very conservative estimate). And that doesn’t include face book posts, or anything else.
When someone rights a tweet, we don’t spend more than a few minutes quick typing down a fast little message, updating people about what we are up to or how we feel, so it only takes a few seconds. Then we hit enter, and poof it’s gone. You can’t save a tweet for further revisions, although you can delete one after it has been sent out. But after that it’s already been seen. Thanks to new technology that alerts you about new tweets all over the place, your phone, email, even your face book.
Because of the speed we use the Internet with we often don’t recognize the things we put out. Most posts are made in a few seconds, with little more than a few seconds of revision, sometimes none at all. This leads to us making mistakes grammatically, but more importantly, not thinking about what we are writing… at least not as much as we should.
Granted, we are thinking about who we are writing to, electronic communications are all made with a specific audience in mind, but often we don’t think of secondary, or even tertiary audiences, the near epidemic of sex-ting scandals in everything from high schools to the white house shows us that people just aren’t thinking about the possibilities of where their data can go.
We assume that our data is safe and sound, we know only our friends, and those who follow us get our tweets, and our privacy settings are locked up tight, so we are safe right?
Nope, Internet security comes down to your ability to self-sensor over the Internet, if you want to have an illicit conversation, go somewhere private, don’t assume the Internet is a safe place to send an email with your credit card numbers (or a private photo) to someone. The Internet is plenty safe, but just like most household appliances, although they have measures to protect you from normal hazards, it isn’t modeled for the stuff you might try to do with it. Similarly, twitter, Facebook, Gmail, Gmail +, and all the other companies out there want you to be public, the biggest part of the service they give is a way to meet new people. Therefore they will set your default settings to be as public as possible, and maintain your privacy when it comes to your log-in data and such, not what you post (they assume you want to .
But for those of us who still want to use these public mediums, pay attention to what you are using. Treat the Internet the same way you treat writing a letter, or a note, it’s written proof of your ideas, and opinions. And when you tweet your standing on the corner of 5th and Rye, maybe you could just say a corner, it probably won’t ruin your totally lol inducing observation about the lady next to you, and you will be better off in the long run.
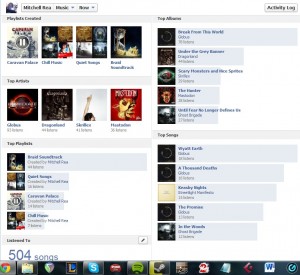 Connecting the music streaming service Spotify to accomplishes two things: First, Spotify automatically posts any and every song you listen to on the service on your Wall, regardless of whether you listen to the song from the Spotify cloud or from your own hard drive via Spotify. Second, Spotify posts detailed specifics of what songs, albums, and playlists you’ve listened to to your profile. All of sudden, people can learn that you don’t just listen to Keasby Nights, you’ve listened to it 115 times since you downloaded Spotify.
Connecting the music streaming service Spotify to accomplishes two things: First, Spotify automatically posts any and every song you listen to on the service on your Wall, regardless of whether you listen to the song from the Spotify cloud or from your own hard drive via Spotify. Second, Spotify posts detailed specifics of what songs, albums, and playlists you’ve listened to to your profile. All of sudden, people can learn that you don’t just listen to Keasby Nights, you’ve listened to it 115 times since you downloaded Spotify.